Hello all,
I found a vulnerability on MTPutty (latest ver. 1.6.0.176) function. This vulnerability allows you to read the SSH connection password (Cleartext).
What is the MTPutty?
PuTTY is the most popular SSH client for Windows. One, and probably the only one, of PuTTY drawbacks is that you need to start a new copy of PuTTY every time you open a new connection. So if you need e.g. 5 active connections you run 5 PuTTY instances and you have 5 PuTTY windows on the desktop.
MTPuTTY (Multi-Tabbed PuTTY) is a small *FREE* utility enabling you to wrap unlimited number of PuTTY applications in one tabbed GUI interface. You are still continue using your favorite SSH client, but you are no longer messing around with PuTTY windows – each window will be opened in a separate tab.
Proof of Concept
Step 1: Open MTPutty and add sample SSH connection
Step 2: Go to properties tab and select “Password in command line (SSH only)” option. As you can see, password is masked over there but we can see cleartext on Win32_Process.
Step 3: Then connect to the server and open powershell
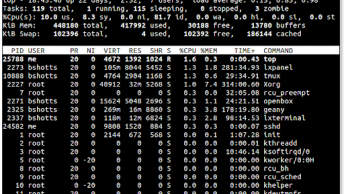
Step 4: And run “Get-WmiObject Win32_Process | select name, commandline | findstr putty.exe”
Step 5: Enjoy your password 🙂