Hello all, I’m going to show you how can we analyze some Microsoft Office document with Olevba tool. First of all we have to download Olevba on Linux system and run python setup.py install command. So, it will start the installation.
How it works?
Olevba is checks the file type: If it is an OLE file (i.e MS Office 97-2003), it is parsed right away. If it is a zip file (i.e. MS Office 2007+), XML or MHTML, Olevba looks for all OLE files stored in it (e.g. vbaProject.bin, editdata.mso), and opens them. Olevba identifies all the VBA projects stored in the OLE structure. Each VBA project is parsed to find the corresponding OLE streams containing macro code. In each of these OLE streams, the VBA macro source code is extracted and decompressed. Olevba looks for specific strings obfuscated with various algorithms like Hex, Base64, StrReverse, Dridex or VBA expressions also cans the macro source code and the deobfuscated strings to find suspicious keywords, auto-executable macros and potential IOCs.
About VBA Macros
See this article for more information and technical details about VBA Macros and how they are stored in MS Office documents.
Analyzing a file
We can use olevba –help command for showing all useful commands.
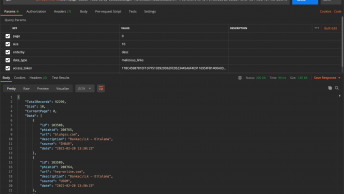
So, I have a malicious CSV file and this file executing some powershell command over VBA macros.

Let’s analyze this file with Olevba.
olevba -a -d –decode –deobf filename.csv
| -a, –analysis | display only analysis results, not the macro source code. |
| -d | detailed mode, display full results (default for single file) |
| –decode | display all the obfuscated strings with their decoded content (Hex, Base64, StrReverse, Dridex, VBA). |
| –deobf | Attempt to deobfuscate VBA expressions. |

As you can see, the List_27.csv download malicious JAR files remotely by running a powershell command. Also you can see URL address to which it communicates.
See other defensive security posts.